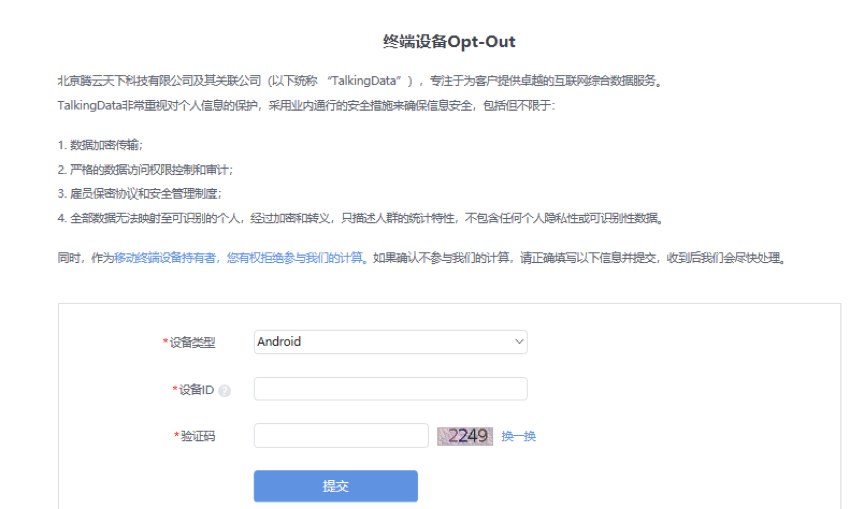
| Name of the Permission | Specific Function of the Permission | Purpose of the Permission | Timing of Permission Requests | Related Products |
| INTERNET | Initiating Network Connection. | To permit applications to establish online connectivity and transmit data. | Data analysis is invoked as needed, for instance, when reporting data is required. | App Analytics, Ad Tracking |
| ACCESS_NETWORK_STATE | Obtaining the present status of the network. | To permit applications to check the connectivity status, and suspend data transmission in instances ofnetwork irregularities. | Data analysis is invoked as needed, for instance, when data reporting is required in a connectedstate. |
| READ_PHONE_STATE | Obtaining device information. | To generate de-identified unique identifiers for end-users. | Data analysis is invoked as needed, for instance, during ad attribution processes. |
| ACCESS_WIFI_STATE | Obtaining WiFi information. | To generate de-identified unique identifiers for end-users, and identify fraudulent traffic. | Data analysis is invoked as needed, for instance, during ad attribution processes. |
| WRITE_EXTERNAL_STORAGE | Granting permission for apps to inscribe data onto external storage. | To store device information, and document logs. | Data analysis is invoked as needed, for instance, during ad attribution processes. |
| ACCESS_FINE_LOCATION(optional) | Obtaining relatively precise location information. | To rectify end-user geographic distribution data, enhancing the precision of report data, and identifyfraudulent traffic. | Data analysis is invoked as needed, for instance, when analyzing the geographical distribution ofend-users is required. |
| ACCESS_COARSE_LOCATION(optional) | Obtaining coarse location information. | To identify fraudulent traffic. | Data analysis is invoked as needed, for instance, when analyzing the geographical distribution ofend-users is required. |
| GET_TASKS(optional) | Obtaining the status of the app utilization. | To enhance the precision in evaluating end-user engagement levels. | Data analysis is invoked as needed, for instance, when analyzing the active status of end-users isrequired. |