Brand Growth
Prevent fraud and drive growth in brand value.
| Name of the Permission | Specific Function of the Permission | Purpose of the Permission | Timing of Permission Requests | Related Products |
| INTERNET | Initiating Network Connection. | To permit applications to establish online connectivity and transmit data. | Data analysis is invoked as needed, for instance, when reporting data is required. | App Analytics, Ad Tracking |
| ACCESS_NETWORK_STATE | Obtaining the present status of the network. | To permit applications to check the connectivity status, and suspend data transmission in instances of network irregularities. | Data analysis is invoked as needed, for instance, when data reporting is required in a connected state. | |
| READ_PHONE_STATE | Obtaining device information. | To generate de-identified unique identifiers for end-users. | Data analysis is invoked as needed, for instance, during ad attribution processes. | |
| ACCESS_WIFI_STATE | Obtaining WiFi information. | To generate de-identified unique identifiers for end-users, and identify fraudulent traffic. | Data analysis is invoked as needed, for instance, during ad attribution processes. | |
| WRITE_EXTERNAL_STORAGE | Granting permission for apps to inscribe data onto external storage. | To store device information, and document logs. | Data analysis is invoked as needed, for instance, during ad attribution processes. | |
| ACCESS_FINE_LOCATION(optional) | Obtaining relatively precise location information. | To rectify end-user geographic distribution data, enhancing the precision of report data, and identify fraudulent traffic. | Data analysis is invoked as needed, for instance, when analyzing the geographical distribution of end-users is required. | |
| ACCESS_COARSE_LOCATION(optional) | Obtaining coarse location information. | To identify fraudulent traffic. | Data analysis is invoked as needed, for instance, when analyzing the geographical distribution of end-users is required. | |
| GET_TASKS(optional) | Obtaining the status of the app utilization. | To enhance the precision in evaluating end-user engagement levels. | Data analysis is invoked as needed, for instance, when analyzing the active status of end-users is required. |
| Name of the Permission | Specific Function of the Permission | Purpose of the Permission | Timing of Permission Requests | Related Products |
| INTERNET | Initiating Network Connection. | To permit applications to establish online connectivity and transmit data. | Data analysis is invoked as needed, for instance, when reporting data is required. | App Analytics, Ad Tracking |
| IDFA | Obtaining IDFA. | To generate de-identified unique identifiers for end-users. | Data analysis is invoked as needed, for instance, during ad attribution processes. | |
| LOCATION(optional) | Obtaining location information. | To rectify end-user geographic distribution data, enhancing the precision of report data, and identify fraudulent traffic. | Data analysis is invoked as needed, for instance, when analyzing the geographical distribution of end-users is required. | |
| WIFI(optional) | Obtaining WiFi data. | To identify fraudulent traffic. | Data analysis is invoked as needed, for instance, during ad attribution processes. |
| Name of the Permission | Purpose of the Permission |
| ohos.permission.INTERNET | To permit applications to establish online connectivity and transmit data. |
| ohos.permission.APP_TRACKING_CONSENT(optional) | To generate de-identified unique identifiers for end-users. |
| ohos.permission.GET_NETWORK_INFO | To permit applications to check the connectivity status, and suspend data transmission in instances of network irregularities. |
| ohos.permission.GET_WIFI_INFO(optional) | To identify fraudulent traffic. |
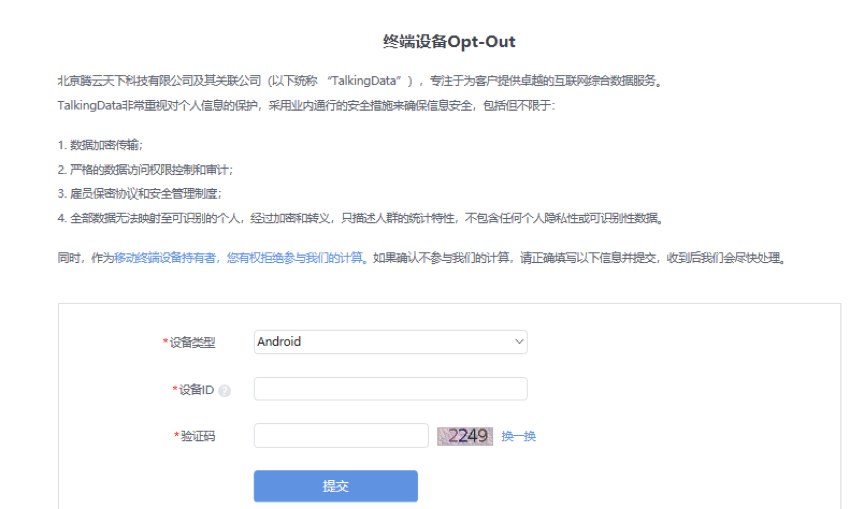
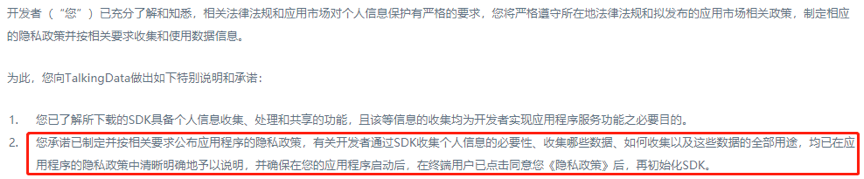
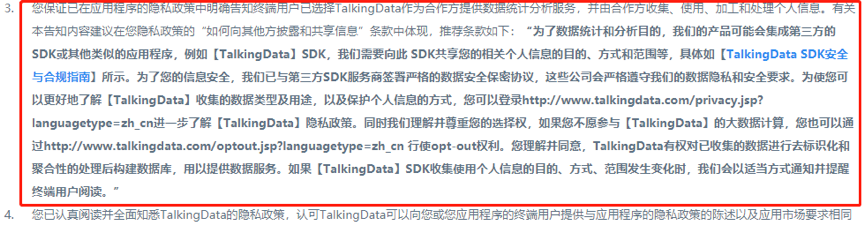
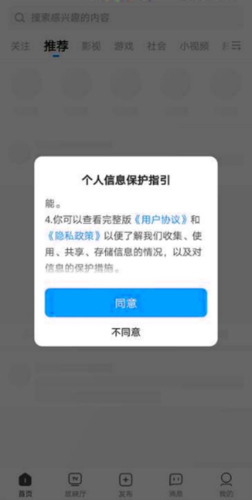 1.8 Instructions for End-Users to Exercise Their RightsEnd-users have the option to request the exercise of their rights related to personal data processing from either party involved. Upon receiving any requests from end-users regarding personal data processing activities associated with the TalkingData SDK, please promptly notify us within 24 hours, and let us work together to address these requests.To facilitate end-users in directly exercising their rights to opt-out, you should inform them that they can utilize the TalkingData opt-out mechanism to exercise their right to withdraw consent. Once an end-user exercises their opt-out right, their personal information will no longer be processed in any manner, and their consent will not be frequently asked for. The link for TalkingData opt-out is as follows:http://www.talkingdata.com/optout.jsp?languagetype=zh_cnTalkingData strongly recommends embedding this opt-out link within your "Privacy Policy" to enable end-users to conveniently exercise their opt-out rights.
1.8 Instructions for End-Users to Exercise Their RightsEnd-users have the option to request the exercise of their rights related to personal data processing from either party involved. Upon receiving any requests from end-users regarding personal data processing activities associated with the TalkingData SDK, please promptly notify us within 24 hours, and let us work together to address these requests.To facilitate end-users in directly exercising their rights to opt-out, you should inform them that they can utilize the TalkingData opt-out mechanism to exercise their right to withdraw consent. Once an end-user exercises their opt-out right, their personal information will no longer be processed in any manner, and their consent will not be frequently asked for. The link for TalkingData opt-out is as follows:http://www.talkingdata.com/optout.jsp?languagetype=zh_cnTalkingData strongly recommends embedding this opt-out link within your "Privacy Policy" to enable end-users to conveniently exercise their opt-out rights.